With cyber-attacks on the rise, companies are transforming their approach to security monitoring from reactive towards intelligence-driven security. We empower your security teams and your business to perform better in the digital world with a Next-Generation Security Information and Event Management (SIEM) platform and Security Operations Centre (SOC)
ASPEN (Advanced Security Processing ENgine) leverages Big Data technologies to deliver real-time threat intelligence, forensics and incident response capabilities. We combine ASPEN with its SOC (Security Operations Centre) services to a solution that addresses the widest spectrum of internal and external threats organisations face today. Built by a team of security professionals with 20+ years of experience in cyber threat prevention, ASPEN is a leading next-gen SIEM (Security Information and Event Management) solution that brings features for security data collection, analysis and automated threat remediation.
We operate global. ASPEN can be easily deployed anywhere and our security experts are taking care of your protection from several security operations centres around the world. Scalability is a key point of our business, we are ready to open new SOCs when we close a deal with an anchor client in one country or when the business volume in a country requires us to be closer to the clients. We are always looking for local/regional partners to join our forces in a local/regional SOC.
store unlimited amount of data
protect private data in real time
get any log from years ago in less than 10 sec
detect connections with threat hosts in real time
deceit attackers and block them
detect attacks by events correlation
track visually any of your systems or users
process 50,000+ events per second on a single host
ASPEN is the result of an outstanding experience at the highest level and around the world. The technical team behind ASPEN was forged in the first line of defending critical infrastructure and ensuring that major events can carry on without experiencing cyber security problems. They are the unseen soldiers that can also protect your business.
1️⃣ ASPEN creates digital clones as active traps 2️⃣ ASPEN performs both historical and real time (<5ms) correlation 3️⃣ ASPEN offer visual reconstruction (“forensics on a click”) 4️⃣ ASPEN does data anonymisation and pseudonymisation in real time 5️⃣ ASPEN performs real time correlation with Threat Intelligence data 6️⃣ ASPEN integrates with 80+ anti-viruses 7️⃣ ASPEN performs automatic noise events elimination 8️⃣ ASPEN offer real time auto remediation
Know Your Enemy
ASPEN is the only SIEM platform that integrates trap deception tools - digital clones of your IT systems, designed to entice attackers. Besides reducing false positives, ASPEN’s digital traps also allow your teams to acquire valuable knowledge about the latest attack vectors, which gives your company a valuable head start over adversaries.
Google-Like Search
High-speed analytics powered by a modern Big Data Lake platform for processing large volumes of data in real-time. ASPEN platform enables security professionals to query data at lightning fast speed - over 50 million events/msec.
Empower Security Teams
Real-time event correlation capabilities provided by ASPEN enable your security teams to proactively manage risk. A 3D view from a single web console simplifies monitoring. Digital forensics, based on real-time data, can be quickly transformed into insights that help shorten containment time.
Adapted To Your Business
The software is highly flexible and can be tailored to the client’s unique needs. No matter what business logic you have or how complex your IT systems are, ASPEN lets you create correlation rules that meet your business strategy, human factors and industry practices.
Keep The Finger On The Pulse
Unlike other SIEM products, ASPEN embeds business context in security analytics. It delivers alters that give you visibility into end users’ activities on desktops, servers and network devices. This helps to prevent human error and mitigate malicious attacks before any damage can occur.
Deception
Deception is a trick or scheme used to force an attacker to think he is accessing real assets in order to confuse him and detect his action. We provide traps at every possible step of an attacker, from traps deployed at external services to traps deployed at internal memory of every workstation or IoT device.
Auto Remediation
Auto remediation is an approach to automation that responds to security events with automations able to fix, or remediate detected cyber attack.
Threat Intelligence
Threat intelligence is evidence-based knowledge, including context, mechanisms, indicators, implications, and action-oriented advice about an existing or emerging menace or hazard to assets. Threat Intelligence is the process of gathering information about cyber attacks around the world for purpose of recognising similar attacks against your customers.
Automated Pen-Testing
Automated penetration testing is a penetration testing performed by artificial intelligence algorithms, using knowledge based on attack vectors and exploits collected from our traps.
Monitoring And Surveillance
Cyber security monitoring&surveillance provide real-time visibility into an organisation's security posture, by constantly monitoring of people, processes, systems and network events and performing in real time correlation with external and internal data for purpose of detection of cyber security incidents.
How it works
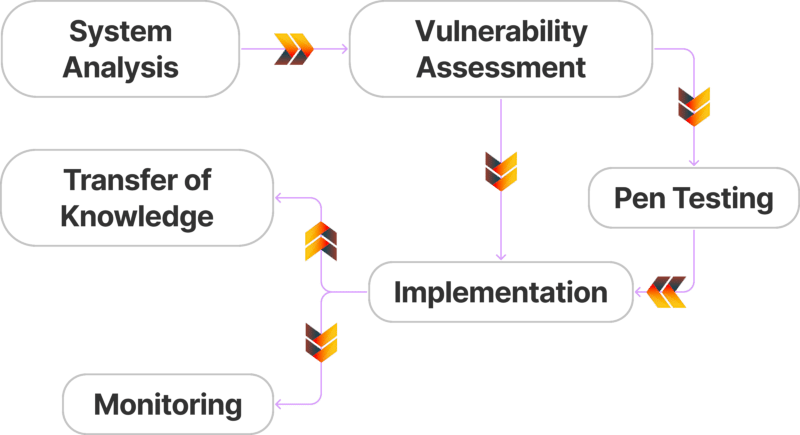
Components
License
Free Resources License
Copyright (c) 2022 PMC
Permission is hereby granted, free of charge, to any person obtaining a copy of these files (the “Resources”), to deal in the Resources without restriction, including without limitation the rights to use, copy, modify, merge, publish, distribute, sublicense copies of the Resources, and to permit persons to whom the Resources is furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice shall be included in all copies or substantial portions of the Resources.
THE RESOURCES ARE PROVIDED “AS IS”, WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION WITH THE RESOURCES OR THE USE OR OTHER DEALINGS IN THE RESOURCES.













